How it works?
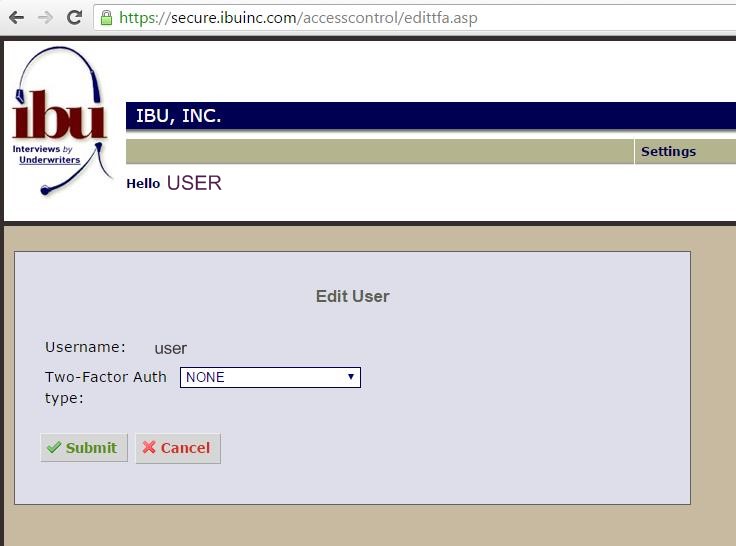
Depending on your situation, we have the following two-factor authentication methods available:
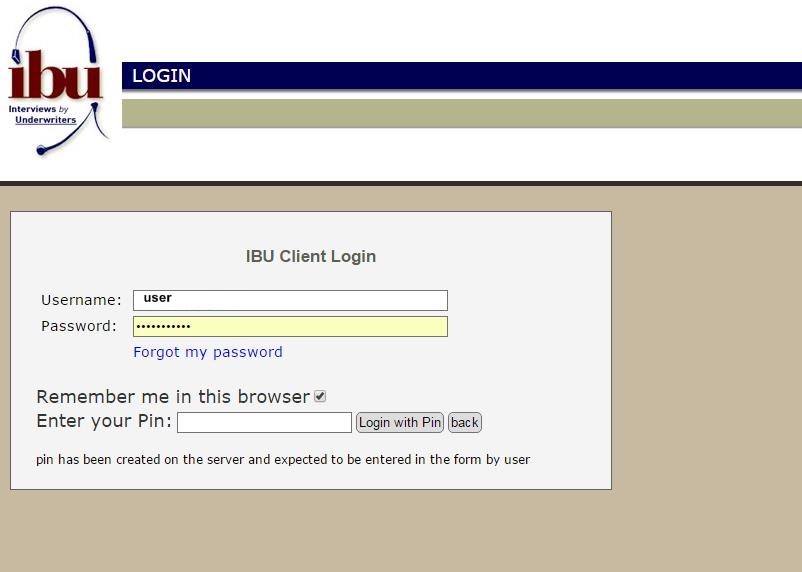
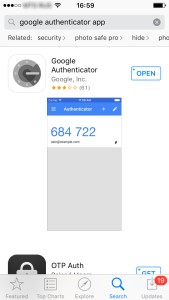
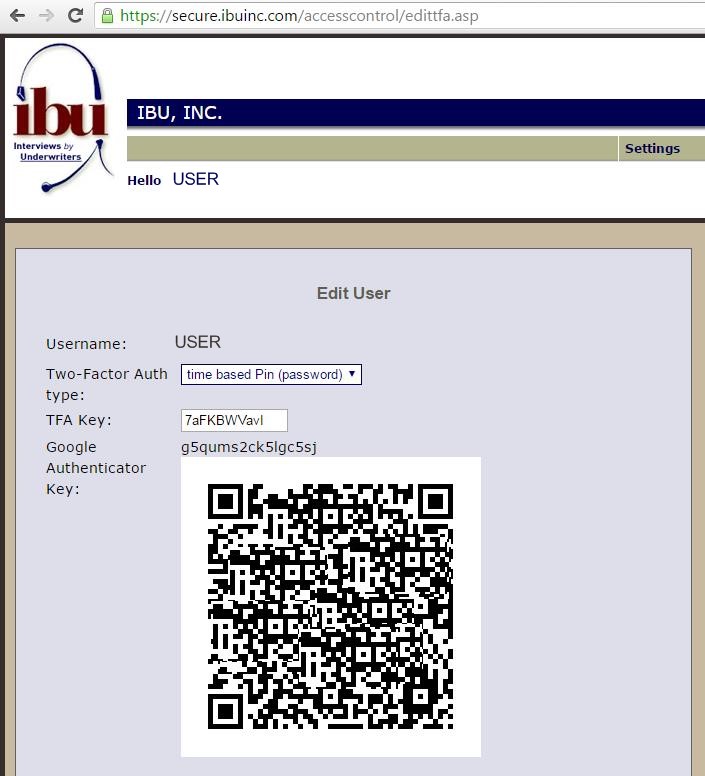
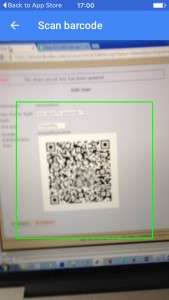
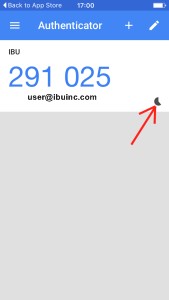
Using your smatphone and google authenticator pincodes

The time-based one-time passwords algorithm generates unique, time-based pincodes and must have a synchronized clock source in order to work properly. TOTP involves generating a temporary, unique pincode that only works for a certain amount of time, typically 30-60 seconds. After the time is up, the pincode will no longer work. A user can generate a pincode by using the "google authenticator" mobile app on a smartphone or tablet. After generating a pincode, a user must type it in manually to authenticate for access.
Using your cell phone and SMS pincodes
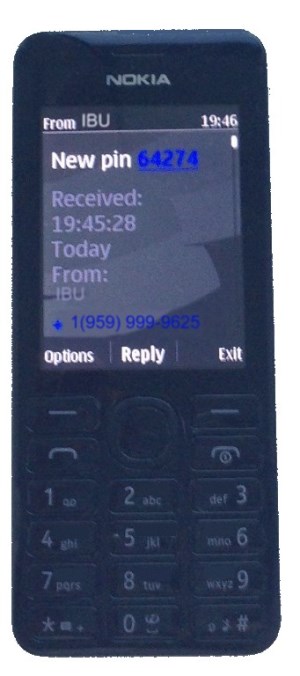
SMS pincodes similar to SMS. The IBU server can generate new, unique pincode by your request to type into the two-factor prompt. It is important that the pincode is delivered over the out-of-band mobile network to your mobile phone and less likely can be intercepted by hackers. After receiving the pincode, a user must type it in manually to authenticate for access. In contrast to TOTP pincodes the SMS pincodes have longer expiration period and considered as less secure. We consider to use it only when the time-based pincodes are not available.
Using the device that you own, the extra security PIN code will be delivered to your cellphone via out-of-band SMS message or created with the google authenticator application on your smartphone or tablet.